Table of Contents
AAA Authentication
AAA in networking terminology is an abbreviation for Authentication, Authorization and Accounting. AAA is what keeps the network secure by making sure only the right and legitimate users are authenticated, that those users have access only to the right network resources and that those users are logged as they go about their business.
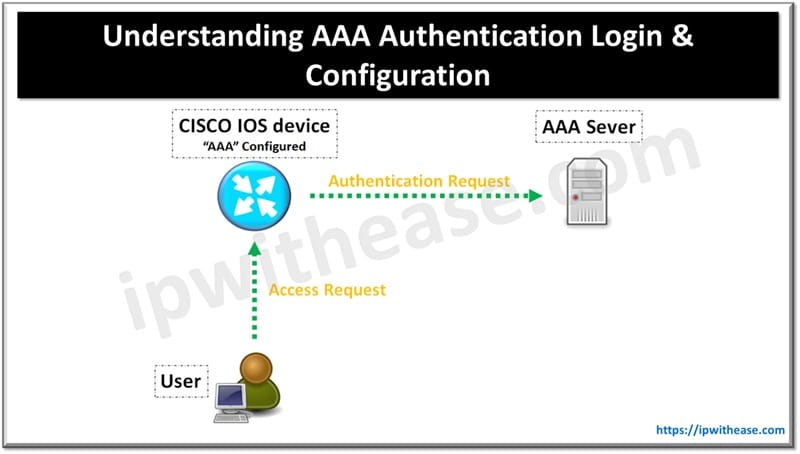
Authentication: Identifies users by login and password.
Authorization: After initial authentication, authorization looks at what that authenticated user has access to do.
Accounting: You can use accounting to see what users do once they are authenticated and authorized. For example, with accounting, you could get a log of when users logged in and when they logged out. In this post we will be configuring AAA on Cisco IOS router with two pre-requisites that should be kept in mind:
- All users logging into the router must authenticate with a username and password to one of two redundant TACACS+ servers.
- Users must be able to log in using a backup local user account stored on the router only if neither TACACS+ server is reachable
Configuring AAA in Steps
Step 1
Create a backup user account
R1(config)#username ipwithease privilege 15 secret ciscoStep 2
Enable AAA
R1(config)#aaa new-modeStep3
Configuring the TACACS+ servers
tacacs-server host 192.168.1.3 key Cisco1 >>>>>For Primary TACAS+ SERVERtacacs-server host 192.168.2.3 key Cisco2 >>>>For Secondary TACAS+ SERVER>Step 4
Define the AAA method list
We need to define a method list which instructs the router to use AAA authentication for terminal logins.
aaa authentication login default group tacacs+ localNow let us understand the above command in parts:
- aaa authentication login : It specifies that the following parameters are to be used for user login authentication. The word default is used instead of a custom name for the list (you can only define one default list for each AAA function).
- group tacacs+: means “use all configured TACACS+ servers.
- local: defines a secondary authentication mechanism; it instructs the router to failover to locally defined user accounts if none of the authentication servers in the first method are reachable.
The above method list handles only the authentication aspect of AAA. By itself, this list only allows us to authenticate as a user with privilege level 1 (user exec mode).
To communicate a heightened privilege level (e.g. privilege level 15, or “enable mode”) from the TACACS+ server, we also need to define an authorization method list
R1(config)#aaa authorization exec default group tacacs+ localRelated: Meaning of line vty 0 4 in configuration of Cisco Router or Switch
Step 5
Enforcing AAA authentication on terminal lines
R1(config)#line console 0R1(config-line)#login authentication default
R1(config-line)#line vty 0 15
R1(config-line)#login authentication defaultNote: These commands won’t be visible under the running-configuration.
Related FAQs
1. Why is AAA important?
AAA enhances security by ensuring that only authorized users access the network, controlling their permissions, and logging their activities for monitoring and auditing.
2. What are the common AAA protocols?
The most commonly used AAA protocols include:
RADIUS (Remote Authentication Dial-In User Service) – Used for network access authentication.
TACACS+ (Terminal Access Controller Access-Control System Plus) – Used for device management authentication.
Diameter – An advanced replacement for RADIUS, providing improved security and scalability.
3. What is the difference between RADIUS and TACACS+?
The main differences are:
| Feature | RADIUS | TACACS+ |
| Protocol | UDP | TCP |
| Encryption | Encrypts only passwords | Encrypts entire packet |
| Usage | Network access control | Device administration |
| Authentication & Authorization | Combined | Separated |
| Accounting | Limited | More detailed |
4. How does AAA authentication work?
AAA authentication follows these steps:
1. The user enters login credentials.
2. The credentials are sent to the AAA server for verification.
3. If valid, the user is authenticated; otherwise, access is denied.
5. What methods can be used for AAA authentication?
AAA authentication can be done using:
1. Local authentication (user credentials stored on the device).
2. Server-based authentication (credentials verified by an external AAA server like RADIUS or TACACS+).
3. Multi-factor authentication (MFA) (using passwords, biometrics, tokens, etc.).
6. How does AAA authorization work?
Once authenticated, AAA checks the user’s assigned permissions to determine what resources they can access and what actions they can perform.
7. What is AAA accounting?
AAA accounting tracks user activities, including:
1. Login/logout times.
2. Commands executed.
3. Data usage.
4. This helps with auditing, billing, and security monitoring.
8. How do you configure AAA authentication on Cisco devices?
Example of enabling AAA on a Cisco router:
Router(config)# aaa new-model
Router(config)# aaa authentication login default group tacacs+ local
Router(config)# tacacs-server host 192.168.1.1 key MySecretKey
This configures TACACS+ authentication, falling back to local authentication if the server is unreachable.
9. What are some best practices for AAA implementation?
1. Use multi-factor authentication (MFA) for stronger security.
2. Store backup user credentials locally in case the AAA server is down.
3. Enable logging and accounting to monitor network activities.
4. Use encryption for authentication traffic.
5. Regularly audit and review AAA policies to ensure security compliance.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj



