Table of Contents
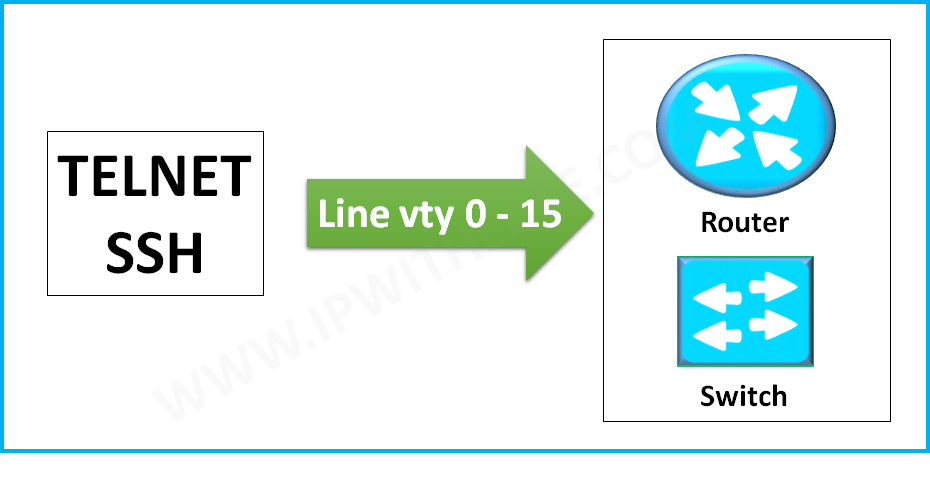
While going through any Cisco Router or Switch configuration, we may come across the term of “line vty 0 4” or “line vty 0 15“.
Let’s discuss these keywords in more detail and their requirement in the configuration of the Cisco Router or Switches –
What is line vty?
The term “vty” stands for Virtual teletype. VTY is a virtual port and used to get Telnet or SSH access to the device. VTY is solely used for inbound connections to the device. These connections are all virtual with no hardware associated with them.
Here’s a breakdown of key points related to “line vty”:
- Purpose: It allows network administrators to connect to and manage Cisco devices remotely.
- Configuration: Administrators can configure various settings on these lines, such as access control, authentication, and authorization.
- Usage: You access the configuration mode for vty lines through the command-line interface (CLI) of the device.
Related Blog – VTY Password
The abstract “0 – 4” means that the device can allow 5 simultaneous virtual connections which may be Telnet or SSH. In a way, we may say that 5 (0 – 4) are connection ports to the Router or Switch. In fact, we may have connection ports up to 16 (0 – 15).
Scenario Example
Here is an example where we configure telnet access to a cisco device and password for telnet facility –
R3(config)#line vty 0 4
R3(config-line)#password Cisco
R3(config-line)#login
R3(config-line)#exitIn this example:
- line vty 0 4 indicates you are configuring vty lines 0 through 4, which means you can have up to 5 simultaneous remote connections.
- password, sets the password for remote access.
- login requires users to provide the password before accessing the device.
By securing and properly configuring vty lines, network administrators can effectively manage and maintain their Cisco devices.
line vty 0 4 vs line vty 0 15
There is no major difference between line vty 0 4 and line vty 0 15. The only difference lies in the number of virtual terminal lines they configure:
line vty 0 4
- This command configures the first five virtual terminal lines, numbered from 0 to 4.
- This means the device can support up to 5 simultaneous remote connections.
line vty 0 15
- This command configures the first sixteen virtual terminal lines, numbered from 0 to 15.
- This means the device can support up to 16 simultaneous remote connections.
Implications
- Simultaneous Connections: line vty 0 4 supports fewer simultaneous remote connections compared to line vty 0 15. The former supports up to 5 connections, while the latter supports up to 16 connections.
- Scalability: If you anticipate needing more remote sessions for administration, monitoring, or other tasks, configuring line vty 0 15 provides greater flexibility.
- Resource Usage: More vty lines may use slightly more resources, but this is typically negligible. However, it’s something to consider in very resource-constrained environments.
Example Configurations
line vty 0 4:
Router(config)# line vty 0 4
Router(config-line)# password your_password
Router(config-line)# login
Router(config-line)# exitline vty 0 15:
Router(config)# line vty 0 15
Router(config-line)# password your_password
Router(config-line)# login
Router(config-line)# exitRelated FAQs
Q.1 What is a VTY line in Cisco devices?
A VTY (Virtual Teletype) line is a virtual terminal line used for remote access to a Cisco device. It allows administrators to manage the device via Telnet or SSH.
Q.2 How many VTY lines can be configured on a Cisco device?
The number of VTY lines varies by device model. Common configurations include 5 lines (0-4) and 16 lines (0-15), but some devices may support more or fewer lines.
Q.3 How do you enable SSH on VTY lines?
To enable SSH on VTY lines, you need to configure the device for SSH and then apply it to the VTY lines:
Router(config)# hostname your_router_name
Router(config)# ip domain-name your_domain
Router(config)# crypto key generate rsa
Router(config)# ip ssh version 2
Router(config)# line vty 0 4
Router(config-line)# transport input ssh
Router(config-line)# endQ.4 How do you restrict access to VTY lines using access control lists (ACLs)?
You can restrict access to VTY lines by applying an ACL:
Router(config)# access-list 10 permit 192.168.1.0 0.0.0.255
Router(config)# line vty 0 4
Router(config-line)# access-class 10 in
Router(config-line)# endQ.5 How can you monitor active VTY sessions on a Cisco device?
Use the show users command to display active VTY sessions:
Router# show usersQ.6 What are some best practices for securing VTY lines?
- Use SSH instead of Telnet for encrypted communication.
- Set strong passwords.
- Limit the number of VTY lines to the minimum necessary.
- Apply ACLs to restrict access.
- Use login banners to display unauthorized access warnings.
- Configure idle session timeouts with the exec-timeout command.
Q.7 How do you set an idle timeout for VTY lines?
To set an idle timeout, use the exec-timeout command:
Router(config)# line vty 0 4
Router(config-line)# exec-timeout 5 0
Router(config-line)# endThis example sets the timeout to 5 minutes and 0 seconds.
Q.8 What happens if all VTY lines are in use?
If all configured VTY lines are in use, any new remote connection attempts will be denied until a VTY line becomes available. Administrators may need to disconnect idle sessions or increase the number of VTY lines if the device supports it.
Related Video For better Understanding
Related – What is CEF?
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)