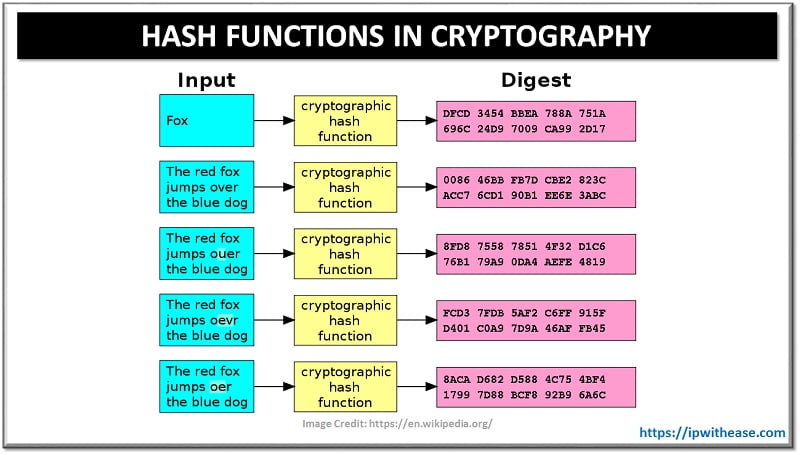
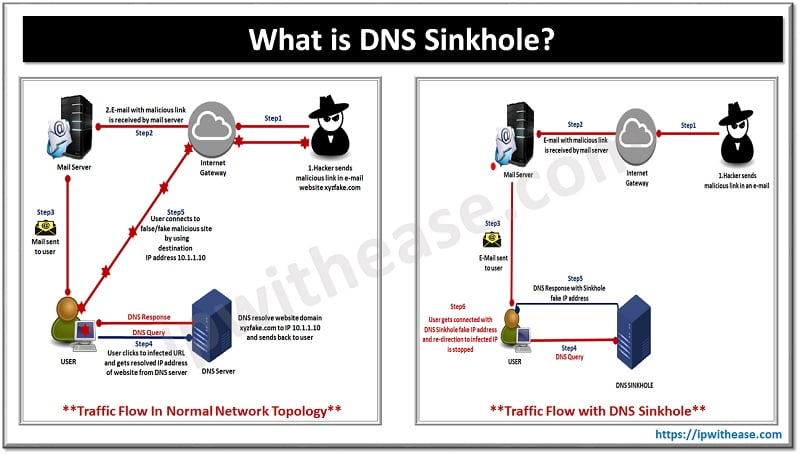
With the incredible advancement of the Internet, it has become more and more craze to set up virtual private networks (VPNs) within organizations. VPNs have been there around for years and have multiple varieties available.
VPNs provide means to create a safe and encrypted connection over a less secure public network such as the Internet. VPN is a way to extend a private network using a public network and they use a variety of tunnel protocols to establish secure connections.
Today we look more in detail about various types of VPNs which exist and protocols commonly used by VPNs, how VPNs function, its advantages and use cases etc.
What is a Virtual Private Network?
VPN is a type of private network which uses a public communication system such as the Internet. It has become more popular as more and more organizations are opting for a remote working model where their employees may be based out of some remote locations. VPN uses tunnelling or virtual point to point connection to create a secure and encrypted channel or connection between the system and other devices residing within the same VPN.
Types of VPN ( or Virtual Private Network)
Let’s look at different types of VPNs more in detail.
Remote Access VPN
It is also known as a client to Site VPN. The data between the business user with VPN client and corporate site with a VPN server is passed via a VPN tunnel and the internet.
The encrypted connection is set up between remote users via VPN client to VPN server; the encrypted connection is known as tunnel which protects data flows through this tunnel. The remote access VPN can be used by home users or private users or two regions that bypass regional restrictions on the Internet.
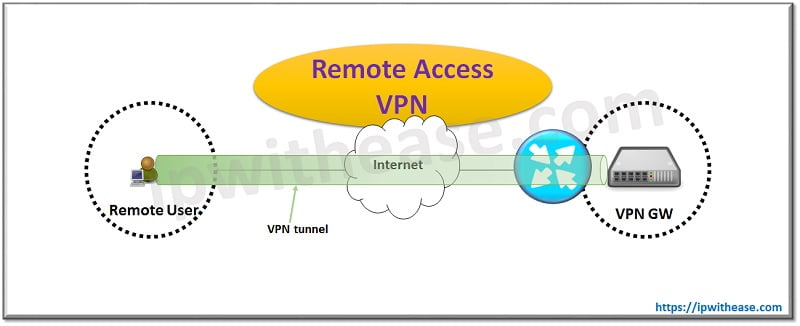
VPN tunnels can be created using tunnelling protocols such as
- Point to point tunnelling protocol,
- Layer 2 tunnelling protocol,
- Secure socket layer (SSL),
- Transport layer security (TLS),
- Internet protocol security (IPS) and
- OpenVPN.
Advantages of Remote access VPN
- Secure and scalable encrypted tunnels across a public network using a client software
- Cost savings using toll free number to call ISP
Site to Site VPN
Site to Site VPN can be Intranet based or Extranet based. Intranet VPN is created by joining multiple LANs into a single private network.
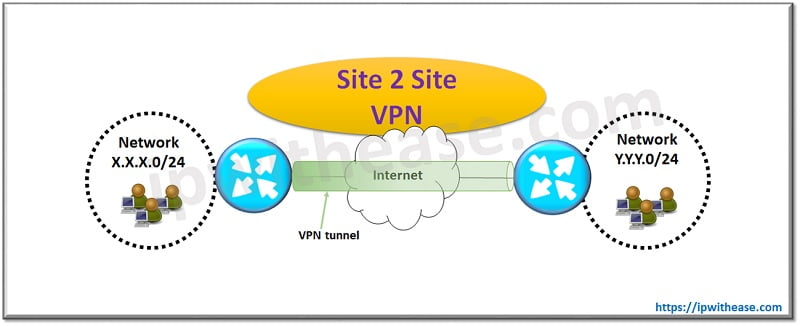
Advantages of Site-to-site Intranet based VPN
- Low costs, tunnelled connections with rich VPN services like IPSec encryption and QoS to ensure reliable throughput
- Cost savings over frame relay and leased lines
In case of Extranet based VPNs if a company has a close relationship with another business entity such as partner, supplier or customer they can build an extranet VPN which connects one organization LAN to another organization LAN and allows multiple organizations to have a shared environment.
Advantages of Site-to-site Extranet based VPN
- Extends WANs to business partners
- Safe Layer 3 security
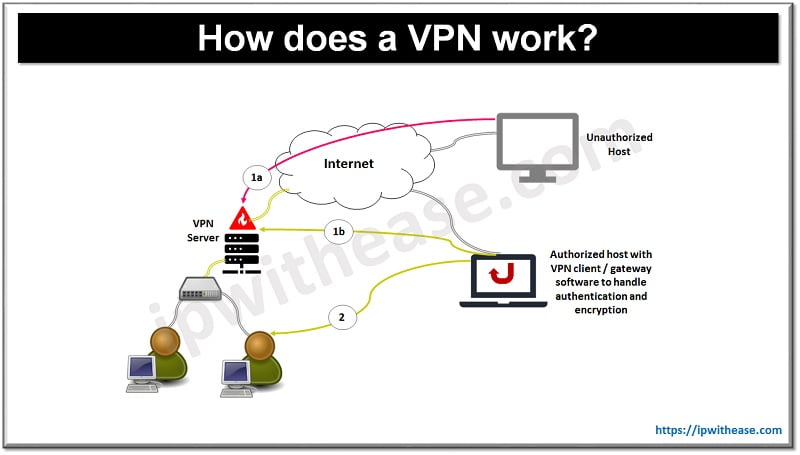
How does a VPN work?
Virtual Private Network (VPNs) Protocols
VPN providers provide various types of VPN protocols in their services. Each protocol has its own advantages and limitations. Different protocols have different ways to provide protection. Let’s look at some commonly used protocols in VPNs:
- PPTP (Point to Point tunnelling protocol) – PPTP is the most widely used VPN protocol, but it has the weakest security encryption as compared to its other counterparts. However, it is easy to set up and used for decades and used by many cheap VPN providers to minimize the cost of running their virtual network businesses. It gives faster access and access to various blocked sites and can be used on all platforms.
- Open VPN – It is an open-source VPN technology which makes it possible to establish a highly secure private connection for devices. It has 256-bit encryption and high configuration on many platforms. Very stable in protecting against threats. OpenVPN is for mobile devices.
- L2TP (Layer 2 tunnelling protocol) – This is similar to PPTP but it is more secure than PPTP and less secure than OpenVPN. It is also slower then OpenVPN however it is considered easy to setup and compatible to all modern devices and operating systems
- IPSec (Internet protocol security) – This is quite similar to L2TP; it has similar security and vulnerabilities to L2TP. This is usually used to encrypt the IP network which you use so all data packets are encrypted during transmission. When combined with other security protocols it can provide security enhancements for those protocols.
- SSL VPN – This secure socket layer VPN is a security used for encrypting network communications. SSL VPNs prevent unauthorized 3rd parties from spying and eavesdropping on communications and also provide protection against Man in the Middle attacks which are not new and quite common.
Continue Reading:
Site to Site VPN vs Remote Access VPN
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj