Data security holds an unparalleled significance in our world. Whether you’re a small business owner, a manager at a large corporation, or an individual concerned about your personal information, it’s essential to understand the measures you can take to protect your data. This article will guide you through the intricacies of data network security, and how it can be leveraged for data security. You’ll learn about the different strategies and tools and how to integrate them into your security protocol.

What is Network Security?
To grasp the significance of applying network security tools for data security, it’s crucial first to understand what network security and data security are. Network security involves implementing measures to protect a computer network from unauthorized access or threats, which could be intentional attacks from specific individuals or random malware infections. On the other hand, data security is about protecting data from destruction or unauthorized access.
You can think of network security as the moat around your castle, keeping out unwanted intruders. Data security, however, is the lock on your castle’s treasure chest, ensuring that even if someone gets inside, they can’t access your most valuable assets. Network security and data security go hand in hand – you need a secure network to protect your data and data security measures to ensure your network isn’t compromised.
Protecting Data Security at the Network Level
A recent report indicates a significant surge in ransom DDoS attacks, with a 67% annual and a 24% quarterly increase over last year. This alarming growth rate underscores the importance of robust data security measures at the network level. With effective network protection, businesses can prevent unauthorized access, safeguard sensitive information, and ensure business continuity, even in the face of escalating cyber threats such as ransom DDoS attack
Some methods you can use to protect your data include:
- Implement Network Security Measures: Network security is a primary method for protecting data at the network level. This involves using tools and techniques such as firewalls, intrusion detection systems, and secure network architecture to prevent unauthorized access and threats.
- Use Data Security Platforms: Advanced data security platforms offer a range of sophisticated features to ensure robust protection of information. These platforms typically include encryption, multi-factor authentication and intrusion detection systems to maintain the integrity and confidentiality of data.
- Establish Strict Access Controls: By adopting a set of stringent controls, you can prevent unauthorized access to files, databases, and accounts on your network. This includes setting up user permissions and ensuring only those who need access to specific data have it.
- Regularly Update and Patch Systems: Ensuring your systems are always up-to-date is crucial in data protection. Regular updates and patches can fix vulnerabilities that attackers might exploit, thus boosting your network’s security.
- Employ Encryption Technologies: Encryption converts data into an unreadable format, making it inaccessible to unauthorized individuals. By using strong encryption algorithms and secure key management practices, sensitive information can remain protected even if it falls into the wrong hands.
- Regular Audits and Reviews: Conduct regular audits of your network security program to check its effectiveness. This allows you to identify and rectify any shortcomings, ensuring that your security measures continue to offer robust protection.
Designing a Data Network Security Program
Designing a data network security program is a complex but necessary task. It involves not just choosing the right security tools but also integrating them for maximum effectiveness. This is where integrated security and data monitoring capabilities come into play. Here are some recommendations to help you design a data network security program:
- Understand the Network Infrastructure: Get a clear picture of your network’s structure, including all devices, connections, and data flows. This baseline understanding is essential to identify potential vulnerabilities and to design a security system that effectively covers all areas.
- Conduct a Risk Assessment: Evaluate the potential threats to your network and the damage they can cause. Understanding these risks will help you prioritize security measures and allocate resources effectively.
- Choose the Right Security Tools: Select the appropriate network security tools based on your risk assessment. These tools should be capable of detecting, preventing, and mitigating potential threats.
- Integrate Security Tools: Rather than using standalone security tools, integrate them for maximum effectiveness. This allows for a more comprehensive view of security events and helps quickly identify and respond to threats.
- Implement Data Monitoring: Regular network data monitoring can help detect anomalies that signal potential security breaches. This proactive approach can prevent major damage by identifying threats early.
- Regularly Update Security Measures: As cyber threats evolve, so should your network security measures. This includes updating security tools and techniques to defend against new attack methods.
- Training and Communication: Ensure that all staff understand the importance of network security. They should be aware of potential threats, how to respond to them, and the best practices for maintaining security.
- Establish Incident Response Procedures: Develop a comprehensive incident response plan that outlines containment, mitigation, investigation, and resolution steps to address security incidents effectively. Having a well-prepared plan can minimize the potential damage caused by security breaches.
- Implement Access Control Measures: Implement solid access control measures like multi-factor authentication and regularly review user access permissions. Limiting access to authorized personnel can significantly reduce the risk of unauthorized access and data breaches.
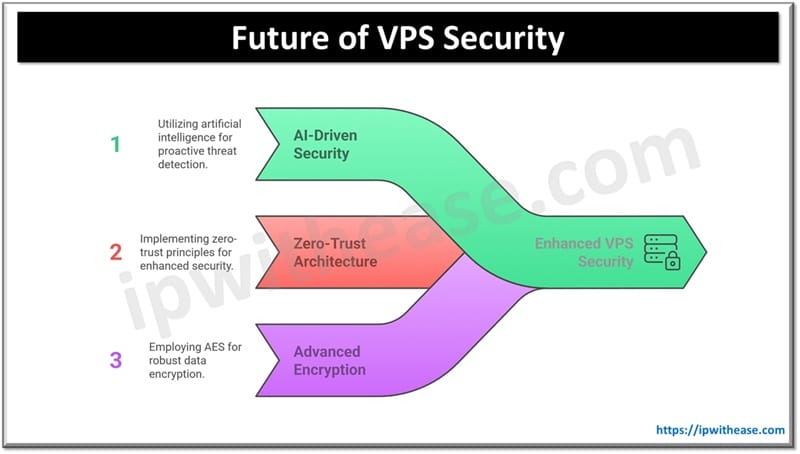
In the world of network security, the only constant is change. As technology evolves and cyber threats become more sophisticated, network security tools must keep up. Some upcoming trends include the use of artificial intelligence in network security, the rise of zero-trust networks, and the increasing importance of cloud security.
In conclusion, applying network security tools for data security is crucial for any organization. By understanding network security, choosing the right tools, and designing an integrated security program, you can protect your data and keep your digital fortress secure. Remember, the best defense is a good offense. Don’t wait for a data breach to happen – take action now to secure your network.
Continue Reading:
Zero Trust Network Access vs Zero Trust Application Access
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.