Table of Contents
In the digital realm, providing a streamlined user experience while ensuring robust security is paramount for any service or application. Single Sign-On (SSO) systems offer an efficient solution by enabling users to access multiple applications with a single set of credentials. This functionality not only improves user satisfaction by reducing the number of passwords they must remember but also enhances security protocols and simplifies management for developers and administrators. This article provides a step-by-step guide on how to implement SSO in web applications, discussing different protocols and best practices.
What is Single Sign-On (SSO)?
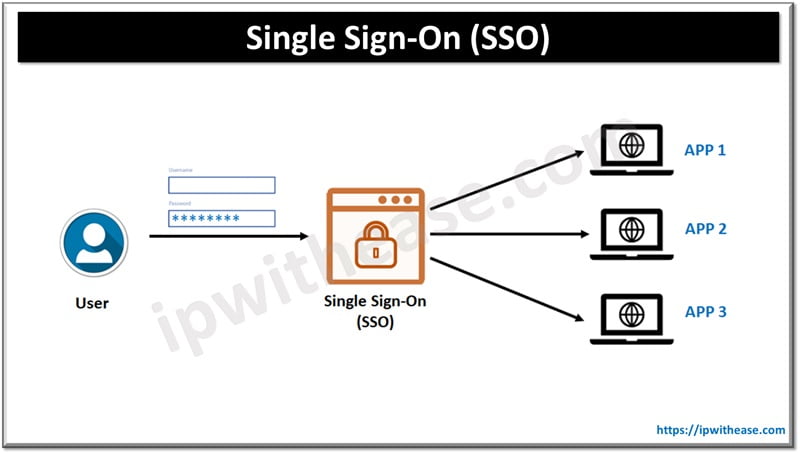
Single Sign-On (SSO) is a user authentication process that allows users to access multiple applications with one login credential. SSO is particularly beneficial in environments where users are required to interact with multiple applications or systems, reducing password fatigue and minimizing the chances of security breaches.
Key Benefits of Implementing SSO
- Enhanced User Experience: Reduces the number of login prompts, making application navigation seamless.
- Improved Security: Minimizes the risk of password-related breaches by reducing the number of credentials users must manage.
- Operational Efficiency: Decreases IT support costs by reducing the number of password reset requests.
How to Implement SSO in Your Web Application
Step 1: Select an SSO Protocol
The choice of protocol is crucial and depends on the specific requirements of your application. Common protocols include:
- SAML (Security Assertion Markup Language): Best suited for enterprise applications, providing extensive security features.
- OAuth: Ideal for applications that require permissions to use resources from another application, like logging into a third-party service.
- OpenID Connect: Builds upon OAuth 2.0, adding an identity layer for authenticating users.
Step 2: Choose an Identity Provider (IdP)
An Identity Provider (IdP) manages the user’s login credentials and other identity data. Popular IdPs include Google Identity, Okta, and Microsoft Azure AD. The choice of IdP should align with the technical needs and existing infrastructure of your organization.
Step 3: Set Up the Identity Provider
This involves configuring the IdP to handle requests from your application. Key tasks include:
- Defining how user credentials are verified.
- Setting up the necessary attributes that the IdP will provide to your application.
- Ensuring secure communication between your application and the IdP.
Step 4: Integrate SSO into Your Application
This step varies significantly depending on the selected IdP and SSO protocol. It typically involves:
- Configuring your application to redirect to the IdP for authentication.
- Implementing logic to handle the response from the IdP, which includes assertions in the case of SAML or tokens for OAuth and OpenID Connect.
Step 5: Implement Session Management
Managing user sessions is critical in SSO environments. This includes setting timeouts, handling session renewals, and ensuring secure session terminations. Proper session management enhances both security and user experience.
Step 6: Testing and Validation
Before going live, thorough testing must be conducted to ensure the SSO integration works as expected. This should include:
- Testing for security vulnerabilities.
- Verifying that all user flows work correctly and seamlessly.
- Ensuring that the system can handle expected loads.
Step 7: Monitor and Maintain
Post-deployment, continuous monitoring is essential to ensure the SSO system operates effectively and securely. This includes regular updates, audits, and compliance checks to adapt to new security challenges and regulatory requirements.
Considerations and Challenges
While SSO can significantly improve user experience and security, it also introduces challenges such as:
- Complexity in Integration: Especially in heterogeneous environments with various legacy systems.
- Dependency on a Single System: Failure in the SSO system can mean loss of access to all integrated services.
- Compliance and Privacy Concerns: Handling and storing user data can be subject to regulatory requirements.
Conclusion
Implementing Single Sign-On is a strategic decision that can enhance user experience, bolster security, and improve administrative efficiency in managing user access across multiple applications. By following the outlined steps and adapting to the specific needs of your web application, you can successfully implement a robust SSO system. As with any significant implementation, ongoing maintenance, and attention to evolving security landscapes are crucial to ensure the longevity and effectiveness of your SSO solution.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.