Table of Contents
Introduction to Firewall Zones
Defining Firewall Zones is a part of the Security framework which needs to be followed while configuring cisco ASA Firewall (In Routed/Layer 3 mode).
Without configuring Zones, the required level of security across assets may not be possible.
“Security Level” indicates how trusted an interface is compared to other interfaces.
As a thumb rule – High-Security level means High trust interface while Low-Security Level means Low trust interface.
Each interface on the ASA is a security zone. Cisco ASA can be configured to have multiple security levels (from 0 to 100).
Related- Cisco ASA NAT
Firewall Security Levels
Below is a description of the ASA firewall security levels –
Security Level 100
This is the highest and most trusted security level of ASA Firewall security level. “Inside” interface is by default assigned this security level.
LAN subnets (Like corporate user subnets etc.) usually come under this category level.
As default Firewall behaviour, Security Level 100 traffic can reach any other lower security Levels configured on the same Firewall.
Security level 0
This is the lowest and considered least secured Security Level on the ASA Firewall. By default outside Interface of ASA Firewall comes under Security Level 0. Generally, the Internet or other untrusted links are terminated over this Zone.
Default Firewall behaviour is to block any traffic from untrusted Zone (Security Level 0) trying to reach any destination of another security level.
Security level 1 – 99
Security Level from 1 to 99 can be assigned to multiple Zone-like DMZ may be assigned Security Level 50. Another case is extranet Zone which may be assigned customised Security Level of 50.
Related- Internet vs Extranet
It’s essential to highlight that traffic from Higher Security Level may reach a destination in Lower Security Level Zone. For e.g. – LAN Zone traffic (Security Level 100) can reach to unsecured Internet Zone ( Security Level 0) however Traffic back from Internet/Outside Zone can’t reach Inside/LAN Zone.
Access List needs to be implemented to complete communication from a lower security zone to a higher security zone.
Example Scenario: “Security Zone” on ASA Firewall
A sample lab scenario will help us with the configuration of “Security Zone” on ASA Firewall –
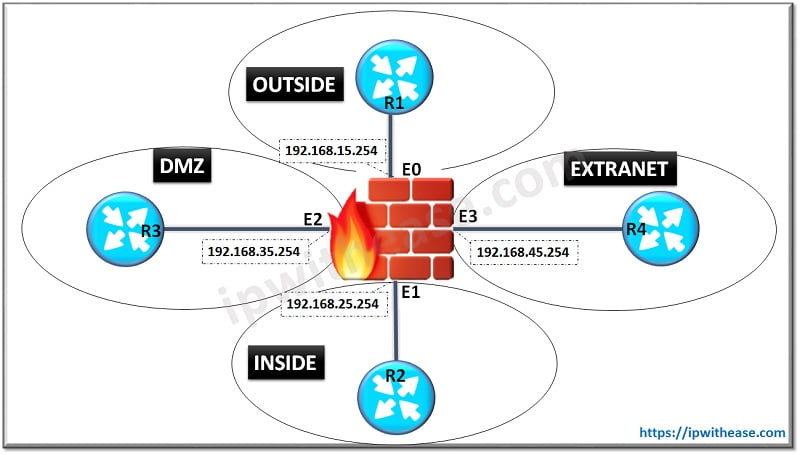
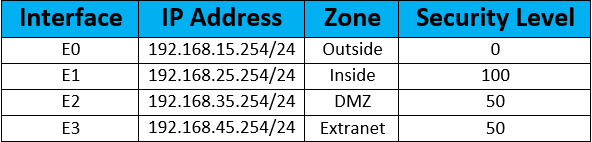
Below is the Interface and Zone configuration on ASA Firewall
ASA(config)# interface E0ASA(config-if)# nameif INSIDE
INFO: Security level for “INSIDE” set to 100 by default.
ASA(config-if)# ip address 192.168.15.254 255.255.255.0
ASA(config-if)# no shutdown
ASA(config)# interface E1
ASA(config-if)# nameif OUTSIDE
INFO: Security level for “OUTSIDE” set to 0 by default.
ASA(config-if)# ip address 192.168.25.254 255.255.255.0
ASA(config-if)# no shutdown
ASA(config)# interface E2
ASA(config-if)# nameif DMZ
INFO: Security level for “DMZ” set to 0 by default.
ASA(config-if)# security-level 50
ASA(config-if)# ip address 192.168.35.254 255.255.255.0
ASA(config-if)# no shutdown
ASA(config)# interface E3
ASA(config-if)# nameif EXTRANET
INFO: Security level for “EXTRANET” set to 0 by default.
ASA(config-if)# security-level 50
ASA(config-if)# ip address 192.168.45.254 255.255.255.0
ASA(config-if)# no shutdown Below command, will verify whether the configuration has been implemented on Interface “E0” of Firewall –
ASA# sh run interface e0
interface Ethernet0nameif OUTSIDE
security-level 100
ip address 192.168.15.254 255.255.255.0In the same way, we can verify for E1 to E3 Interfaces.
Hope this article would have cleared your doubt around firewall security level.
Related Video for Better Understanding
Continue Reading:
Read these articles to know more about firewall:
Stateless vs Stateful Firewall
Router IOS Firewall vs Network Firewall
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj