In this article, we will discuss Static NAT configuration on Cisco ASA firewall and Cisco ASA Static NAT example.
Cisco ASA Static NAT

Static NAT is primarily required when a Data Center or Hub site has WEB Facing Server in DMZ Zone (or Inside Zone if no DMZ) and Users over the Internet need to access the Application of Web Facing server. The applications may be Web (HTTP) Server, Email Server or even FTP server. Below is a sample scenario where an Application server is Hosted in DMZ Zone and needs to be accessed from outside (Internet) Zone. For testing, R1 Router is the users sitting over the Internet while R2 is the Web Server in DMZ Zone –
Related- Cisco ASA Object Group
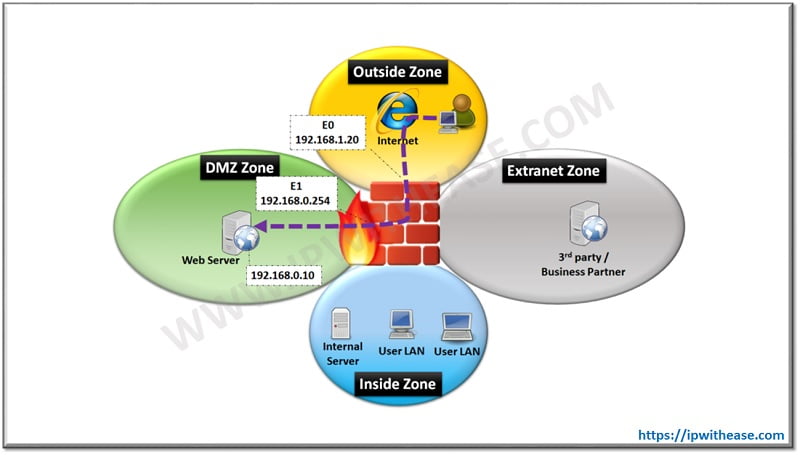
Cisco ASA Static NAT Example
Below is the configuration for ASA version 8.3 or older.
1st step is to create Network Object named “WEB-SERVER” and then the translated IP address. Static NAT statement will define which outside address to use.
ASA(config-network-object)# nat (DMZ,OUTSIDE) static 192.168.1.10
2nd step includes creating the access list (extended) which allows any source IP address to connect to real IP address 192.168.0.10
Now that configuration is in place , next we will configure Router R2 (configured as DMZ Server for testing) with Line VTY password “cisco” –
R2(config-line)#password cisco
R2(config-line)#login
For verification, telnet from R1 (host over Internet) to R2 (192.168.0.10) as below –
User Access Verification
Password:
R2>
The nat translation over ASA can be viewed by “show xlate” command as below –
Flags: D – DNS, d – dump, I – identity, i – dynamic, n – no random,r – portmap, s – static
NAT from DMZ:192.168.0.10 to outside:192.168.1.10 flags s
Related- Static vs Dynamic NAT- NAT Types
Related- ASA Firewall Security Guide
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj