Table of Contents
Securing network traffic while in transit is one of key requirements of security. VPNs are usually used to encapsulate IP packets and provision a secure tunnel to transmit private traffic in encrypted form over public networks. Point to Point IPsec tunnels are cumbersome, so network leaders like Cisco had developed their own proprietary technology to secure communication between groups thus eliminating the need to negotiate point to point IPsec tunnels between group members.
Today we look more in detail about Cisco proprietary technology known as GETVPN, its features and use cases , advantages and disadvantages and so on.
About GETVPN
GETVPN or Group Encrypted Transport VPN is Cisco implementation of GDOI standard. GDOI is a group domain of interpretation and it is defined in RFC 6407. It was established originally to allow encryption of multicast traffic. Secure multicast applications could be audio or video broadcasts and GETVPN is used for encrypting any type of traffic over private networks. MPLS VPNs use it for encryption.
It establishes a set of rotating encryption keys that a group uses and shares. Any group member can encrypt data and any other group member can decrypt data without setting up a point-to-point tunnel with another group member. The entire system is tunnel-less. GETVPN uses the original IP header and the underlying routing is preserved.
Components of GETVPN
It has four main components :
- GM (Group member)
- KS (Key server)
- GDOI (Group domain of interpretation)
- IPsec
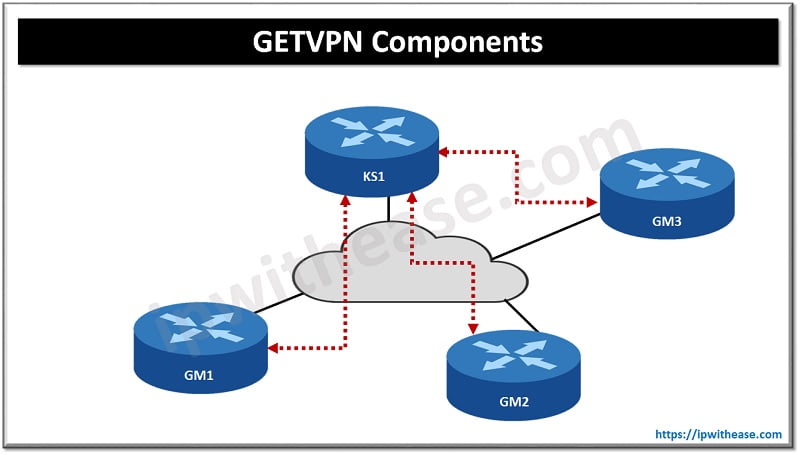
GM (Group member)
GM (Group member) is a VPN router and is a member of a group which encrypts traffic with other GMs. All GMs have same IPsec SA so encryption could be performed by any GM
KS (Key server)
KS (key server) is ‘caretaker’ of the GM group. Group registrations and authentication of GMs is taken care of by KS server. Any GM who wants to join the group is required to be successfully authenticated in the group and sends encryption keys and policy to be used within the group.
When GM is making an attempt to register to KS server , it verifies group ID and IKE credentials, post checking it sends back below to GM server :
- The security policy used by group
- Two keys:
- KEK (Key encryption Key) – used for encrypting rekey messages, this is used by GMs to decrypt relay messages from KMs
- TEK (Traffic encryption key) – The IPsec SA which is used by all GMs to encrypted traffic within each other
The KS will send relay message when the current IPsec SA is about to expire or when there is any change in security policy. Relay can be done using unicast or multicast. In unicast GM sends an acknowledgement to the KS post receiving the key. When KS don’t receive acknowledgement after three transmissions it deletes the GM. Multicast method is more scalable but it does not support acknowledgement.
KS ensures registration, authentication and security policy and keys but it is not a GM and neither becomes part of the GM group and also not install IPsec SA.
GDOI (Group domain of interpretation)
GDOI (Group domain of interpretation) is protocol used between GM and KM. It is protected with ISAKMP which is used in regular IPsec. All ISAKMP options related to authentication such as pre-shared keys or certificates can be used here . In phase 2 two keys (KEK and TEK) are sent by KS server and the security policy. KS keeps a track of SA lifetime and rekeys a new SA when the old one is about to expire. Rekey messages are signed with a private key to safeguard from anyone pretending to be KS server. GETVPN doesn’t use volume-based SA expiry.
IPsec
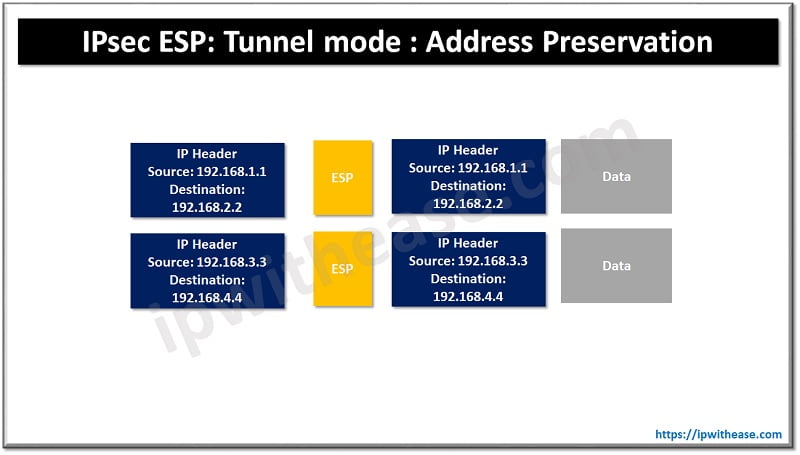
IPsec – uses ESP (Encapsulating security payload) which is similar to IPsec VPNs. It supports tunnel mode to encapsulate the entire IP packet and adds a new IP header. GETVPN uses tunnel mode with address preservation which means the inner IP header is copied to the outer IP header. The network can route packets based on the actual destination and find the best path for each destination. GETVPN is meant for private networks where full reachability is not an issue between all sites.
Features of GETVPN
- Any to Any large scale encrypted communication
- No tunnel overlay along with native routing
- Improves application performance – optimal for QoS and multicast support
- Seamless integration with multicast infrastructures without multicast replication issues
- Preservation of IP source and IP destination address during IPsec encryption and encapsulation
- Transport agnostic – private LAN / WAN, FR/ATM , IP and MPLS
- Large scale any-to any connectivity using group IPsec program instantly
How to configure GETVPN
Here we use a topology as an example to see how to configure GETVPN. We have one key server and two group members. The cloud in the center will represent a private WAN. OSPF is configured on GM routers to advertise loopback interfaces.
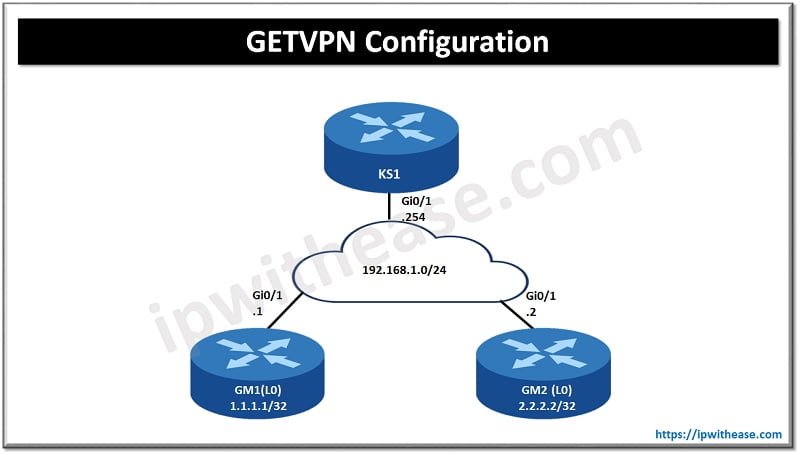
Key server
IKE phase 1 policy
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 5Use a pre-shared key for all GMs
R1(config)#crypto isakmp key MY_KEY address 0.0.0.0GETVPN use IPsec ESP (transform set)
R1(config)#crypto ipsec transform-set TRANSFORM_SET esp-aes esp-sha-hmacAdd transform set instead of crypto profile
R1(config)#crypto ipsec profile IPSEC_PROFILE
R1(ipsec-profile)#set transform-set TRANSFORM_SETCreate a new RSA key pair
R1(config)#crypto key generate rsa modulus 1024 label RSA_KEYSCreate access list to match ICMP traffic
R1(config)#ip access-list extended ICMP
R1(config-ext-nacl)#permit icmp any anyConfigure GDOI group
R1(config)#crypto gdoi group GDOI_GROUP
R1(config-gkm-group)#identity number 123Command to tell router it is KS
R1(config-gkm-group)#server localAdd our own KS IP address
R1(gkm-local-server)#address ipv4 192.168.1.254Inform router to use the RSA key-pair to protect the rekey messages and to send them with unicast:
R1(gkm-local-server)#rekey authentication mypubkey rsa RSA_KEYS
R1(gkm-local-server)#rekey transport unicastConfigure the IPsec policy – add IPsec profile and access list
R1(gkm-local-server)#crypto gdoi group GDOI-GROUP
R1(gkm-local-server)#server local
R1(gkm-local-server)# sa ipsec 1
R1(gkm-local-server)#profile GETVPN-PROFILE
R1(gkm-local-server)#match address ipv4 CRYPTO-ACLNow GETVPN is configured and running.
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj