Performing non administrative activities using an account having admin privileges is not considered a good security practice. Normally users are provisioned with multiple accounts one for normal day to day tasks and one for administrative tasks. There are multiple reasons which drive organizations to monitor and protect the use of privileged (admin) accounts.
Today we look at these two major terminologies and tools – PAM (Privileged Access Management) and PIM (Privilege Identity Management), understand their key differences and use cases.
About PAM (Privileged Access Management)
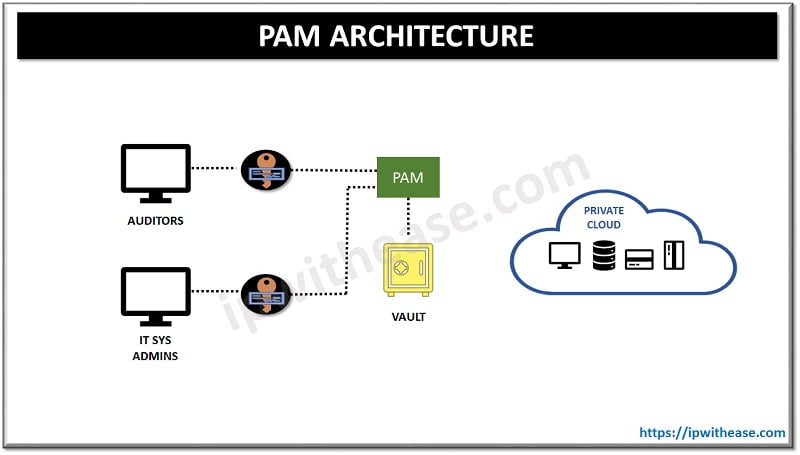
Privileged Access management is a combination of tools and technology in order to secure, control, and monitor access to an organization’s critical information and resources. Privileged Access management subcomponents are shared access password management, privileged session management, vendor privileged access management and application access management.
PAM works on principle of least privilege which means restriction on access rights and permissions and have permissions or rights which are bare minimum required for daily operations of users, programs, systems endpoints and processes.

PAM Pros and Cons
PROS
- Fine grained access control
- Multi factor authentication
- Single sign – on
- Password vaulting
- Auto discovery and customized reporting
- Reduced malware infection and propagation
- Session monitoring
- Deliver temporary credentials to specific groups and users
CONS
- Over provisioning of privileges
- Lack of visibility and awareness of privileges users, accounts, assets and credentials
- Hard coded / embedded credentials
- Lack into visibility for application and service account privileges
- Siloed IAM tool and processes
How does PAM work?
About PIM (Privileged Identity Management)
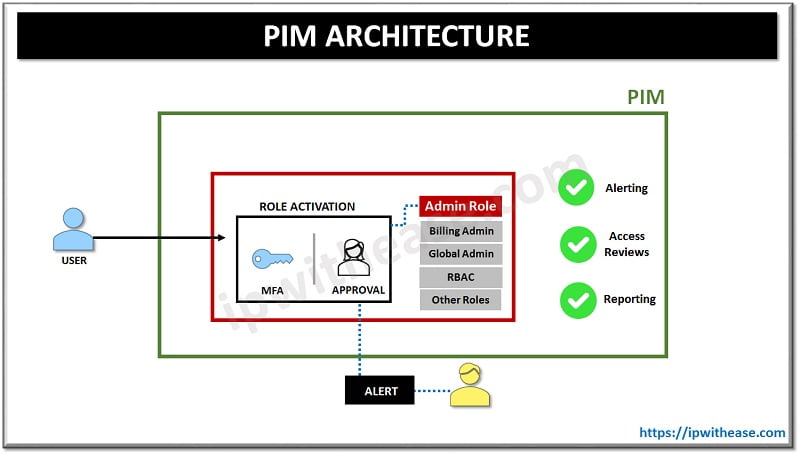
Privileged Identity management (PIM) is wholesome monitoring as well as protection for admin / super users accounts in the organization. A privileged account is an administrative account having authorization to change configuration settings, permissions, adding users, downloading software etc. Privileged Identity management solution secure privileged accounts. These are super admins who have elevated permissions to access critical information.
How does PIM work?
PIM Pros and Cons
PROS
- Provide just in time privileged access
- Assigns time bound access to resources
- Enforce multi factor authentication to activate roles
- Control authentication into privileged accounts
- Scheduled and event triggered password changes
- Event and session logs are captured
- Ability to record access to privileged accounts
CONS
- Ongoing costs are high
- Failing to Discover All Privileged Accounts
Comparison Table: PAM vs PIM
Below table summarizes the difference between the two:
PARAMETER | PAM | PIM |
| Definition | A system used to protect, manage, monitor and control privileges | A system to manage, control, and monitor access to resources having admin/ super user access in the organization |
| Technology | LDAP (Lightweight directory access protocol) and SAML | LDAP |
| Features | -Isolation and scoping of privileges -Just in time administration (minimum time to retain privileges) -Provide time bound access to resources -Enforce multi factor authentication -Approval or denial of privileges based on policy -Secure administrative hosts -Approval / justification for privileges activation | -Identify and keep track of all privileged accounts -Define how super user accounts will be managed -Set up procedures and tools for super user account management -Access reviews to ensure user still need roles -Audit history for external / internal audits -Approvals to activate privileges |
| Applications | One Identity, Foxpass, Hitachi ID etc. | ManageEngine, Microsoft Azure, Okta identity cloud, Auth0 etc. |
Download the comparison table: PAM vs PIM
Continue Reading:
Introduction to IAM (Identity access manager) in AWS
Top 6 Identity and Access Management Companies (IAM)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj