Remote code execution (RCE) attack is more of a class of cyberattacks rather than just one specific type of attack. All RCE attacks share a common ground that revolves around running arbitrary code on some target server by exploiting its vulnerable configurations.
In case of a successful RCE attack, hackers can edit or destroy important files, steal confidential data, perform DDoS (Distributed Denial of Service) attacks, and compromise the entire system. Even worse is the fact that these attacks have become rampant in this day and age, and must be accounted for if you own a website.
Today, we’ll learn more about Remote Code Execution attacks, including how you can prevent them by secure coding practices. In case you run an online business, also check out our best cybersecurity tips.
What Makes RCE Attacks Possible?
Having briefly seen the consequences of a successful RCE attack, we all can agree that this issue must be attended to. Here are some important system vulnerabilities that cause a server to be prone to an attack like this.
- Unchecked external user input
- Bad access control
- Poor authentication measures
- Buffer overflows
Without any further ado, let’s explain each of these vulnerabilities one by one.
1. Unchecked External User Input
A server using external user input and trusting it without taking the necessary safety precautions is always in grave danger. All developers know that trusting user input without verifying it is a bad idea, and therefore it must be taken care of immediately.
Input validation includes checking the type, length, and format of the entered input and verifying if it holds up to the validation criteria or not. This way, attackers are unable to insert malicious commands in their input and can be restrained from remotely running unauthorized code on your server.
Furthermore, input to fixed data structures such as drop-down lists must also be processed through validation checks before being sent to the database. A system without any of these safety measures allows unsanitized user input and is therefore in danger of an RCE attack.
2. Bad Access Control
Giving away root access and administrator privileges where it isn’t absolutely necessary is equivalent to giving a monkey a gun. Access control lists are used to determine the permissions and control the various types of users you have on your server.
If a website has poorly segmented permissions, hackers can get a hold of users with root access and irreparably damage your server. On the other hand, if an account with limited permissions is compromised, the possible damage that a hacker can do is also limited. They will still without a doubt cause trouble, but it won’t be as bad as it would’ve been if they had root access.
This demonstrates how a website with bad access control can be an easy target for RCE attacks. The way to prevent this is obviously to be more diligent in how access and privileges are distributed on your server.
3. Poor Authentication Measures
Next on our list of potential causes for RCE attacks are poor authentication measures. This ties together nicely with using unsanitized user input because if your website doesn’t have proper authentication and management systems, you are at high risk of information theft.
Without good session management and authentication methods put in place, hackers can steal usernames, passwords, session tokens, keys, and much more. Moreover, the same hackers can go on to use these accounts maliciously and meddle with sensitive information.
In short, poor authentication and lack of proper management functions can lead to devastating consequences such as full system compromise.
4. Buffer Overflows
All programmers use buffers in their code to designate a fixed amount of RAM for storing information temporarily. The keyword here is “fixed”. Because buffers work on the basis of fixed memory, bound checking measures must be installed in the code to ensure that they don’t overflow.
When a buffer overflows, it overwrites the data stored in its neighborhood buffers – hence rendering legitimate data useless and destroying it. Hackers can purposely cause a buffer overflow on your system to corrupt important information and damage the server. They can also replace the important bits of information with arbitrary code that can abuse the system.
Preventing RCE Attacks
Having comprehensively covered what RCE attacks are and their causes, let’s now get into how you can prevent them.
- Validate user input
- Properly configure authentication methods
- Install buffer overflow protection
- Apply a firewall
1. Validate User Input
As we saw earlier, one should never trust user input. A good rule is to consider all user input as unsanitized and dangerous. Input validation mechanisms must be put in place to counteract malicious data. Use verification functions that first test the length, format, and type of the user-generated input and only then allow it to run on your server.
Fixed data input such as drop-down lists and selection forms must also be checked if it holds up to the validation criteria or not. This ensures that hackers cannot exploit your website through loopholes or inserting arbitrary code in their inputs. Therefore, input validation is a must.
2. Properly Configure Authentication Methods
Authentication methods are the chief contributor to server security. You can set up all sorts of defense mechanisms on your server but having lousy authentication methods is like leaving the front door unlocked.
Without having sufficient authentication methods put in place, the users of your server are exposed to RCE threats. They can have their passwords and usernames stolen and then used for malicious purposes. In short, make sure you configure your authentication methods properly and give them the attention they need.
3. Install Buffer Overflow Protection
We saw that the commonly-used memory buffers on a server can be exploited by overflowing them. This leads to catastrophic destruction and corruption of important data stored in the memory.
Bound-checking measures must be installed in the server software. A common way of doing this is to write methods that detect buffer overflows and protect against them by adding a canary value – a random but known integer. When the canary value is detected to be overwritten, its antecedent buffer has overflowed. This helps the developer detect buffer overflow and terminate the compromised program.
Installing buffer overflow protection on your system is integral to the safety of the server, and stops attackers from exploiting its vulnerabilities.
4. Apply a Firewall
The next step in securing your code is to start using a firewall on your website. Just like your operating system comes equipped with an efficient firewall to counteract viruses and malware, you can install one on your website too.
Website Application Firewalls, more commonly referred to as WAFs are crucial to prevent automated RCE attacks. They stand at the frontier of your server as security and guard against all sorts of common attacks.
In Conclusion
In this article, we learned about Remote Code Execution attacks, including what they are, how bad their consequences can be, and how you can prevent them by secure coding practices. RCE attacks are pervasive in the online world so you should give them the attention they deserve!
Continue Reading:
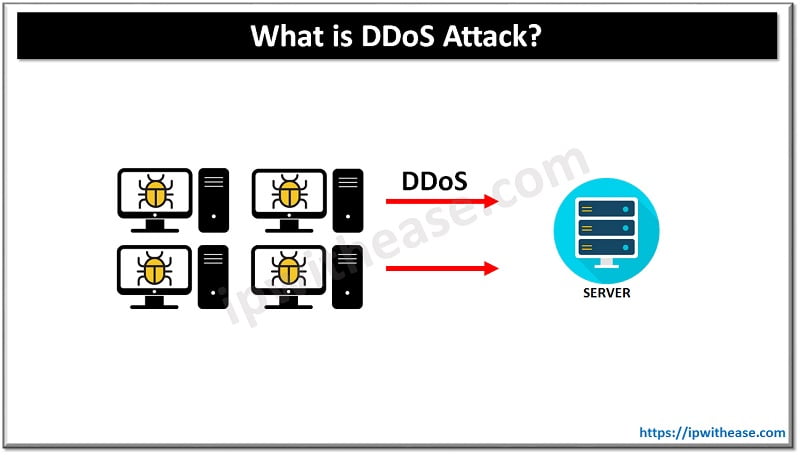
What is DDoS Attack? Distributed Denial of Service Attack
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.