Table of Contents
Introduction to Spear Phishing Attack
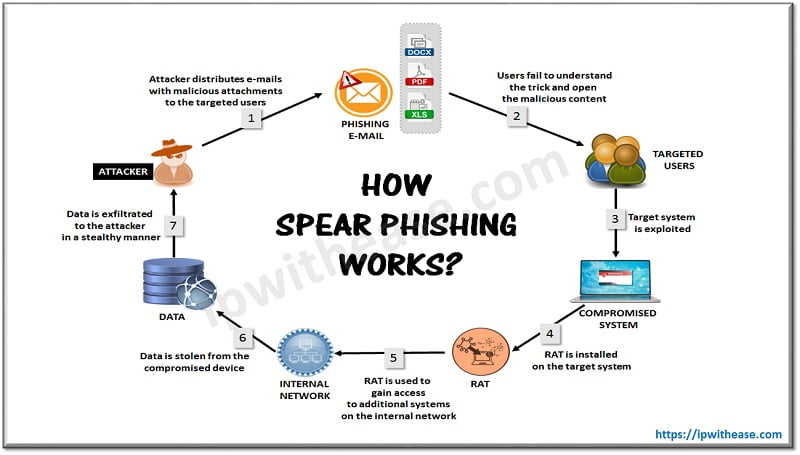
In the cyber community industry nowadays, with the term “Spear Phishing”, we define a targeted attempt to steal private information such as user account credentials or financial information from a specific victim or organization. In order to succeed in this malicious activity, personal details are acquired on the victim such as friendship, hometowns, employers, locations they have frequently visited and what they have recently bought online.
The hackers pretend to be a trustworthy friend or entity to acquire personal information, usually through email or other online messaging platforms. The history of “Spear Phishing” attacks began as a Nigerian prince scam in the mid 1990’s, nowadays they have transformed into well researched and targeted hacker campaigns that are both highly effective and incredibly difficult to mitigate.
While spear phishing attacks may target “smaller size victims”, like a mid-range company employee or a random target chosen on social media platforms. Whaling phishing is looking after the “big size victims.” These attacks often target C-Level executives like CEOs or CFOs to attempt to gather larger payments and more private data.
Mitigation from Spear Phishing Attacks
In the cyber community nowadays there are many theories on how to prevent a spear phishing attack. Most of the commonly used are presented below:
- Profile Sharing Information: The first method to avoid a “Spear Phishing” attack is by considering what personal information you post on the internet. Have a careful look at your online profiles in social media. Try to avoid posting too much personal information for potential attackers to see online. Also make sure that you’ve configured privacy settings to limit what others can see in public views.
- Smart Password Configuration: The second method to avoid a ”Spear Phishing” attack, is by avoiding the use of a single password for every account that you own. Try to introduce different passwords or password variations with complex characters. If an attacker has access to one of your passwords, he can effectively have access to all of your online accounts. Every password that you use should be different from the others as well, such as passwords with random phrases, numbers, and capital letters are the most secure.
- Software Update: The third method to avoid a spear phishing attack is by keeping your software up to date. Vendors provide security patches in future releases and if you see a notification, you should do it right away. The majority of computer systems also include an internal service for security software updates, that should help every user from common attacks. Where possible, enable it in the menu or in your OS interface for your device.
- Data Protection Program: The fourth method to avoid a spear phishing attack that is most wanted for bigger organizations, is the implementation of a data protection program. A data protection program that combines user education around information security best practices and contract based data protection services, will help to prevent data loss.
Spear Phishing vs Phishing
Nowadays, “Spear Phishing” can easily be confused with simple “Phishing” because they are both cyber attacks on users that aim to acquire private information. Although, with the term “Phishing”, it is mainly used for any kind of attempt to trick victims into sharing sensitive information such as passwords, usernames, and credit card information for security reasons.
Unlike Spear Phishing attacks, phishing attacks are not personalized to their victims and are usually sent to many people at the same time. The main objective of phishing attacks is to send a spoofed email that looks as if it is from a legitimate organization to a large number of people.
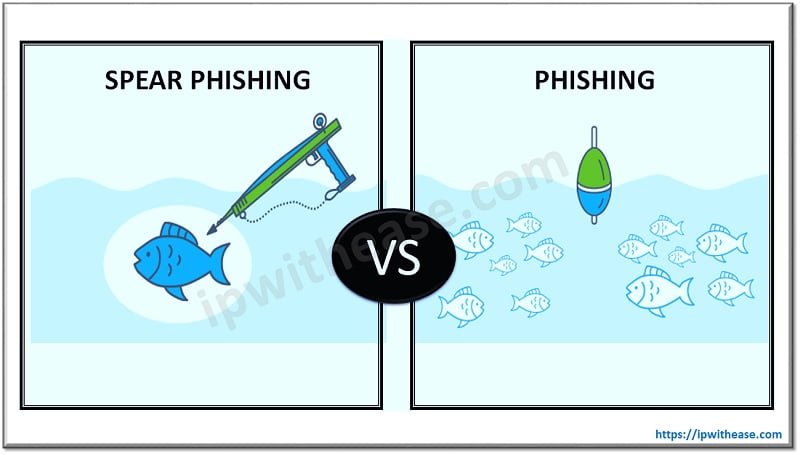
Below table summarizes the difference between the two:

Download the comparison table: Spear phishing vs Phishing
Conclusion
Today we can come to the conclusion that spear phishing attacks are in general a specific type of phishing attacks that are specifically targeted. Like a typical spear phishing attack, which includes an email and an attachment.
The hacker’s email contains information that is specific to the victim user and an attachment looks legitimate. The designing of the message is done in such a way so as to lure the user in carrying out the extra intended tasks.
Hence, it is important that proper security measures are implemented by the organizations in order to avoid the effects of such attacks. The adoption of proper security software will reduce the chances of occurrence of such attacks.
Continue Reading
Introduction to Rainbow Table : Cyber Attack
Whaling Phishing Attack – Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj