Table of Contents
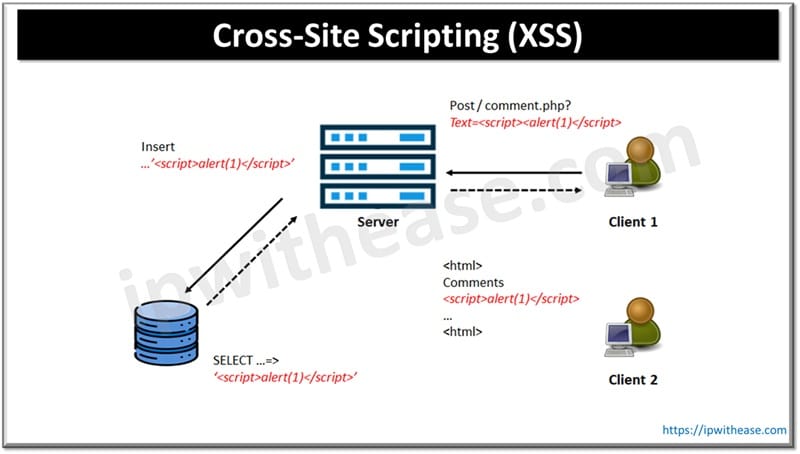
Cross-site scripting is a web vulnerability which allows hackers to masquerade as a targeted user, and carry out actions on behalf of legitimate users and access user data. If a user had privileged access to the application then the attacker might gain full control of the application and its data. Cross site scripting performs manipulation of the vulnerable website and malicious JavaScript is returned to end user.
As the proliferation of the Internet has grown and more and more organizations are moving towards adoption of cloud computing, artificial intelligence and machine learning etc. The cybersecurity incidents are on rise as more and more business applications are hosted and operate over the web which are more susceptible to compromise.
In this article we will learn more in detail about Cross-site scripting, its types, mitigation strategies and vulnerability patching.
Cross-Site Scripting
Cross site scripting allows a third party to execute a vulnerable script in the user browser in lieu of a web application. Cross site scripting vulnerability is one of the most common vulnerabilities. The exploitation could lead to privileges escalation, account compromise, malware infection etc. The malicious website uses JavaScript and reads data from other website responses, embedding them in an iframe, modifying page contents and running scripts. The XSS vulnerability arises when a website does not handle in proper way the input provided to it from the end user and a crafted input is given when an embedded response is executed by the web browser as a JS code block.
Types of XSS
The XSS is of two types:
Reflected XSS
When input is provided every time during its execution it is referred as Reflected XSS. The reflected attacks are carried out by payload delivery directly to victimized users. The victim end user requests a page having a payload which is embedded in the response script.
Store XSS
In the store XSS type of attack, a hacker locates a vulnerability in a web application and then malicious script is inserted into the server. The response having payload is stored on the server so each time when script execution happens on every visit to the website there is no need to submit payload as it is identified and stored as XSS. Most common targets for this type of attack are websites where users can share content such as blogs, social networks, video sharing and message boards.
There is one more type of XSS known as DOM based XSS. It happens when malicious code is inserted into the Document Object Model (DOM) of a web page.
Whichever type is the XSS attack the target is not the application but users of web applications. Severity of XSS could lead to user account compromise, activation of trojan horse programs to modify page contents, tricking users to provide their private data.
Mitigation Strategies for Cross-Site Scripting
- Automated Tools – A variety of tools can be used to detect cross site scripting vulnerabilities in web sites. Such as the Veracode tool which scans web applications for XSS vulnerabilities.
- Code Reviews – Web application source code reviews are used to identify where user input is displayed and accepted such as forms, search fields, interactive elements and comment section.
- Penetration Testing – Annual pen testing to be performed and revalidation of reports with automated tools.
How to Patch XSS Vulnerability
- Application of Input Validation – Implement input validation while checking user input to ensure it contains no suspicious script code and characters.
- Output Encoding Implementation – Output encoding is implemented in user input so it is not intercepted as script code in the web browser.
- Use a Content Security Policy (CSP) – It allows to restrict the types of content web applications could load. This is done to prevent execution of malicious scripts from web browsers.
- Updation to Web Application Software – The web software should be updated to the latest version and patched for security updates.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj