Introduction to SecOps
The term SecOps is defined as a mythology that is implemented mainly for IT Managers in order to enhance the relationship, collaboration and communication between IT security and IT operations working teams. This strategy ensures that the IT organization as a whole can meet the application and network security objectives without compromising on application performance.
SecOps’s implementation involves several steps. The first step is to set priorities and decision based processes. The next step is to share communication channels, software tools and authorizations to information for each team member separately. The last part, Is the update of all the development processes in order to incorporate security at each stage.
The need for SecOps services in the industry, is best illustrated by Gartner’s research, where 99% of the security vulnerabilities exploited in 2019 will continue to exist in the organizations at the time of exploit. In another recent survey by Voke, 79% of the organizations that experienced a security attack indicated that it could have been avoided with a patch or a configuration change in the system’s architecture security.
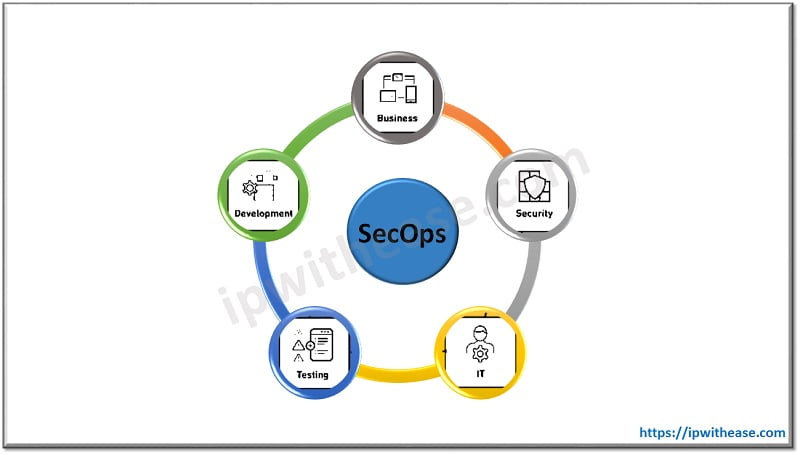
Methods used for SecOps
Most IT organizations are establishing a dedicated security operations center, where SecOps team members collaborate and work together towards these objectives:
- Network Monitoring: SecOps security teams are typically responsible for daily monitoring activity throughout the organization’s IT infrastructure, including private, public and hybrid cloud environments. In addition, network monitoring includes logging of security events, operational status and performance of deployed applications.
- Incident Response: When an unusual or unexpected accident occurs, SecOps teams are responsible for implementing the incident response plan. In this process, Incidents may be reported by users or they can be frequently discovered by network monitoring software tools. Therefore, when a security breach occurs, an incident response team takes the appropriate steps to mitigate the damage and prevent the attacker from further access in the network.
- Forensics and Root Cause Analysis: Forensics analysis of security incidents reflects the ability developed by SecOps to analyze and access information in order to determine the root cause of a security attack, performance issue or another unexpected event on the network. SecOps teams use custom security software tools to conduct root cause analysis, to determine the underlying causes of security issues and mitigate them before they can be exploited again.
- Threat Intelligence: Threat intelligence is a security process with two main steps:
- Obtaining knowledge of possible security threats to the organization and
- Establishing methods to respond to those threats (or proactively prevent them from occurring).
Threat intelligence as a service, can be implemented as a collaborative effort within the SecOps team, the organization as a whole and even between separate business entities.

Advantages of using SecOps
Establishing a dedicated SecOps team, within a security operations center has the following advantages:
- Decreased Security Incidents: Collaborative network monitoring enables early detection of cyber attacks, reducing the number of incidents and protecting information while maintaining compliance with data privacy and security requirements.
- Decreased Security Vulnerabilities: Application code is more secure when it passes the production environment, due to the input parameters from security professionals at earlier stages of the development process. As a result, the IT services of the organization experience decreased security vulnerabilities.
- Decreased Security Distractions: SecOps team members that provide their services in order to automate operations like threat detection and alert monitoring, are distracted less by false positives and provide a better quality of services. This strategy affects focusing on real security threats that require an immediate response.
Related – What is DevSecOps?
Conclusion
With a SecOps implementation, security is the responsibility for everyone in the team and across every aspect of the organization or project task. This strategy has an effect on products and services with fewer vulnerabilities, better compliance and faster patching methods.
The ultimate advantages of embracing includes higher ROI, improved productivity and greater customer satisfaction (All are physical outcomes of adopting SecOps methodology).
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj