Table of Contents
In this blog, we will cover in detail about the OSI model, its layers and network protocols which operate at each layer in OSI model.
In the earlier days of network communication vendors used to implement their own networking models to enable network communication. These models were proprietary and meant to enable product functioning only. Data transportation was possible only between devices created by the same manufacturer. There was a need for a product neutral model so that devices manufactured by different vendors can communicate seamlessly with each other. OSI model was developed to and created to propose a common standard for networking or telecommunication networks.
OSI Protocols
The OSI protocols stack are standards of information exchange and they consist of a set of rules which represent a standard way of making physical connections, cabling, data formats, models for data transmission, error detection and correction etc. These protocols were developed by the International Standard organization (ISO) in 1977.
The OSI protocols operated on seven layers namely – Physical layer, Data link layer, Network layer, Transport layer, Session layer, Presentation layer and Application layer. At each layer data is processed and moved onto the next layer in the hierarchy. The below figure depicts the functioning of each layer and protocols operating at that layer.
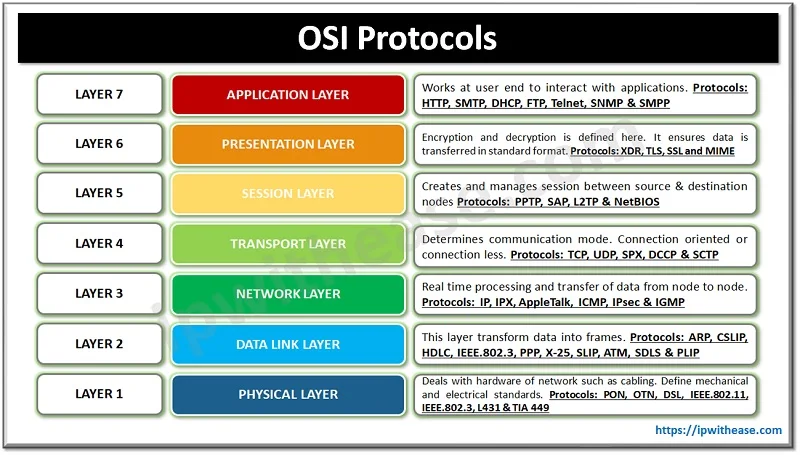
7 Network Layer Protocols
Network layer is responsible for communication between systems in a network. This layer is responsible for delivery of packets from source to destination network. Network layer splits data into fragments (called data packets) and sends them and combines once processing is done. Various protocols are used at this layer to route data to its final destination.
We will learn more in detail about these protocols in this section. Network layer provides guaranteed delivery of packets within bounded delay and in a sequenced manner. Few of the commonly used network layer protocols are:
Address Resolution Protocol (ARP)
ARP protocol performs conversion of logical address (IP address) into physical address (MAC address). If a host wants to know the physical address of another host onto the network it sends an ARP query packet with IP address and MAC address of source host and IP address of destination host and broadcasts it over the network. The ARP packet is received by all hosts on the network and the intended recipient recognizes its own IP address and responds back with its physical address.
The host holding this datagram stores the physical address in cache memory and adds it to the datagram header before responding back to the sender. Reverse Address resolution protocol (RARP) works in reverse mode and operates in the same manner except in this case MAC address of host is known but IP address is not known.
Internet Control Message Protocol (ICMP)
ICMP is a network diagnostic and troubleshooting, error reporting protocol. It is part of the IP protocol suite and uses IP as a carrier because the ICMP packet is encapsulated in an IP packet in its construct. It is the best effort-based non reliable protocol. Network feedback is returned to the host using ICMP. ICMP has dozens of error reporting messages. ICMP handles five types of errors related to:
- Destination unreachable
- Source quench
- Time exceeded
- Parameter problems
- Redirection
IPv4
Internet protocol version 4 is a network layer protocol which addresses and controls information and is used to transport packets in networks. IP and TCP work together to transport packets in a network. Each host is given a 32-bit IP address consisting of network and host ID. The host ID is used to identify a given host on the network whereas network ID is used to identify the network. IP is responsible for packet delivery however TCP puts them in the right order.
IPv6
It is the latest version 6 of Internet protocol. It was established to address limitations of IPv4 so as to accommodate more levels of addressing with IP address size to 128 bit from 32 bit. It also introduced Anycast addressing and removed the concept of broadcasting. Devices can self-acquire IPv6 address and interact within the subnet. The dynamic host configuration protocol (DHCP) servers no longer rely on auto configuration hence the host can still connect even if DHCP is down or not available. IPv6 gives mobility feature to allow Mobile IPv6 enabled devices to roam without changing their IP address.
Related: IPv4 vs IPv6
Internet Group Message Protocol (IGMP)
IGMP is a multicasting communication protocol which uses resources in an efficient manner to broadcast messages/ data packets. Hosts and routers in vicinity use multicasting communication with IP networks. It can be utilized to stream media, games, web conferencing as multicast supports multiple senders and receivers.
Spanning Tree Protocol (STP)
This protocol monitors the network and eliminates the redundant link. To identify redundant links, it uses spanning tree algorithm (STA) which maintains a topology database which is used to find a redundant link. If a redundant link is found then it is disabled. STP divides LAN into segments with the help of bridge.
Bridge is used to connect two segments so when a message is sent it passes through the bridge to reach its destination. Bridge determines if the packet is for the same segment or different segment and works accordingly. This reduces the chances of network choking.
Border Gateway Protocol (BGP)
BGP is used to exchange routing information for the internet and it is used between ISPs. This protocol can connect any internetwork of an autonomous system using an arbitrary topology. The only requirement is that each autonomous system should have at least one router that is able to run BGP and that router connects to one of the other autonomous BGP routers. BGP runs over TCP.
Continue Reading:
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj