Table of Contents
Introduction to SASE
Nowadays, in IT and Cybersecurity communities we define the term Security Access Service Edge (SASE), a network based architecture that combines Virtual Private Networks (VPN) and SD-WAN services with cloud-based security abilities such as web gateways, cloud access security brokers, firewalls, and zero-trust network accessibility.
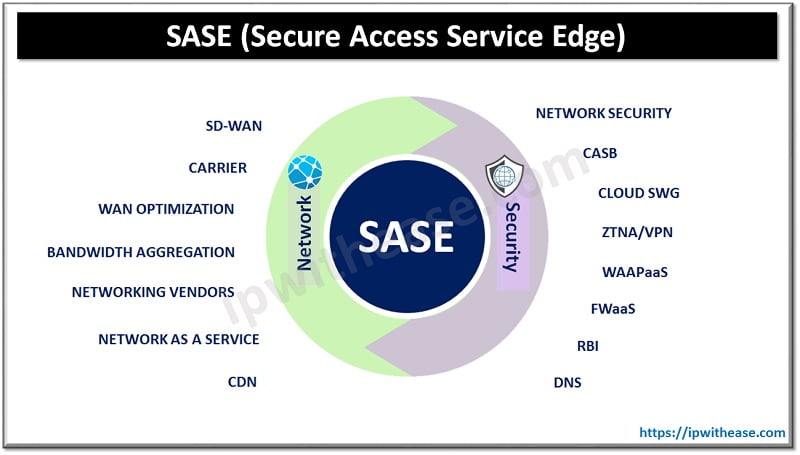
Secure Access Service Edge (SASE) is a term initialized by an analyst firm named Gartner. SASE is designed to be a simplified WAN and security architecture for mobile and global workplaces that is based on cloud applications and data. This works as a solution for backhauling all WAN internet traffic over long distances to a small number of corporate data centers for security functions. This implementation adds network latency because users and their cloud application platforms are globally dispersed, rather than on-premises. Therefore, by targeting services to the edge of the connection source, SASE can eliminate the latency caused by backhauling.
Components of the SASE Model
- SD-WAN: As a general rule SD-WAN technology is known in the industry as a cloud delivered WAN architecture that provides the required building blocks for cloud transformation mostly on enterprises. It helps to predict user’s experience for application integration and provides a flawless multi cloud architecture.
- Cloud Security: Cloud security is defined as a group of technologies and applications that are executed from the cloud services in order to protect against threats and reinforce user experience, data and application policies. It helps the enterprise to manage security by extending controls to remote devices, users and distributed locations anywhere in the network, very rapidly.
- Zero Trust Network Access: Zero trust network access is designed to verify all user’s identities and devices trust before granting security access to authorized applications. It also helps enterprises to prevent unauthorized access, contain breaches and avoid a hacker’s lateral movement on the network.
Advantages of SASE Model Implementation
Gartner cooperation has cited numerous advantages of a SASE architecture for the mobile and cloud enabled enterprises. We have addressed the most essential below:
- Reduced Complexity: The main advantage of SASE Model is the reduced complexity in the cloud model architecture and in the single vendor for all the WAN and security functions and services. In addition, reduced complexity also arises from a single-pass architecture that decrypts the streaming traffic and inspects it with multiple policy engines rather than linking multiple inspection services all together.
- Universal Access: Another very handy advantage of SASE Model implementation is the design of the architecture that provides consistent fast and secure access to any resource from any entity of the network at any location, compared to the single access primarily based around the corporate data center.
- Cost Efficiency: In addition, the SASE Model can provide cost efficiency on the cloud architecture, which reduces the cost to monthly subscription fees. The SASE also consolidates providers and vendors by reducing the number of physical and virtual branch appliances and software agents that the IT department has to buy, manage and maintain in-house. Finally, the cost reduction also is noticed when delegation of maintenance, upgrades and hardware refreshes to the SASE provider is taken into account.
- Network Performance: SASE Model network implementation can also increase performance of applications and services by enhancing the latency routing, which is particularly beneficial for streaming sensitive video and executing VoIP applications. SASE Model providers can also optimize and route network traffic through advanced performance backbones that are contracted with carriers and peer-to-peer partners.
- Consistent Security: Finally, the SASE Model can provide consistent Security via the cloud service for the WAN security functions and the WAN available connections of the enterprise network. It also sets the same policies in Security with the same functions that are delivered by the same cloud service to any access session. Finally, once the SASE provider is adapted to a new threat, the adaption can be available to all edges of the platform.
Conclusion
As digital business transformation constantly changes, then network and security service design patterns constantly need to be reinforced. The main strategy implementation is by shifting the focal point to the identity of the user or network device and not the whole data center. Therefore, security and risk management managers need a converged cloud-delivered secure access service edge to address this shift such as SASE Model.
Continue Reading
Microsegmentation vs Zero trust- What’s The Difference?
What is Cloud Security Posture Management (CSPM)?
Watch Related Video
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj