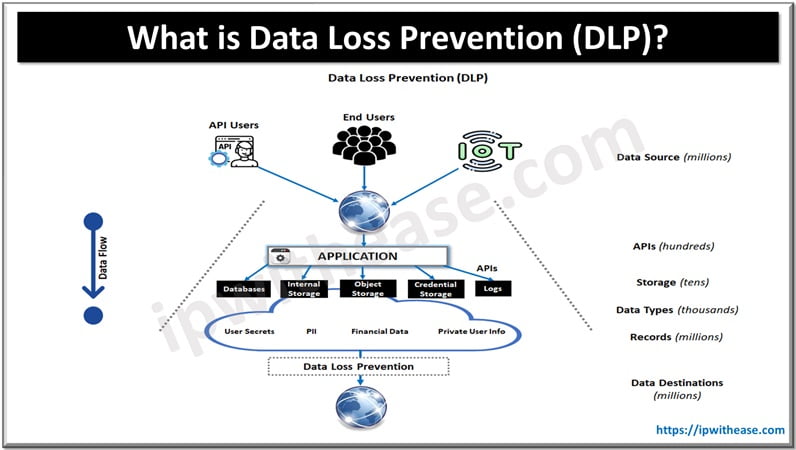
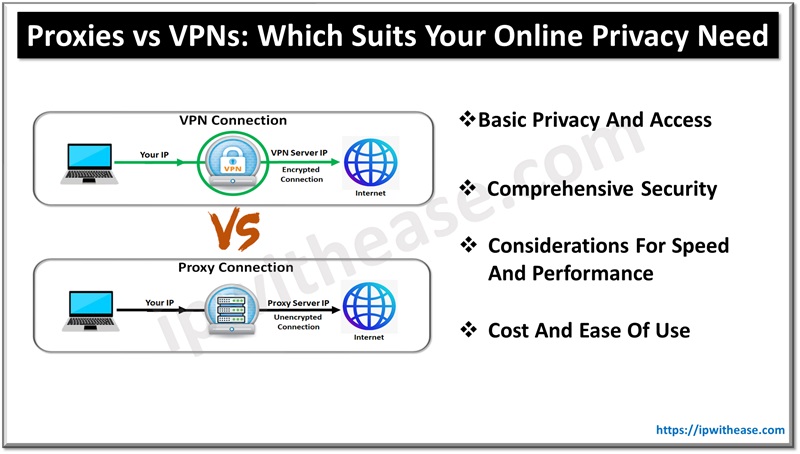
Table of Contents
Introduction to CSRF Attack
Cross-site request forgery (CSRF), also called in the cyber community as “XSRF”, “Sea Surf” or ”Session Riding”, refers to a well-known security vulnerability.
The main concept of such an attack, is the authentication of web applications using cookies. In simple words, the hacker “tricks” the victim into making a request that the victim is unaware.
By executing a “CSRF” attack, a malicious website request is sent to a web application via a different formerly authenticated website. The result is the ability of the hacker to bypass authentication procedures by impersonating the victim using personal credentials and utilize malicious transactions.
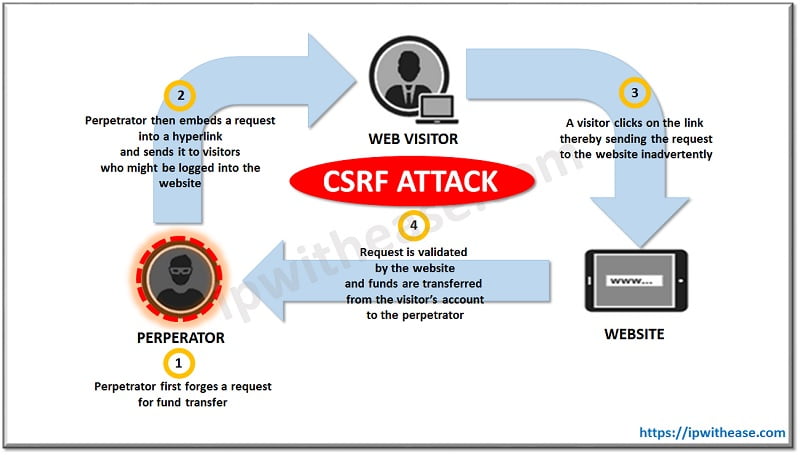
The problem of CSRF attacks is most common on Websites that use session cookies like (Paypal, Online Banking, etc.). On the other hand, since CSRF requires the user to enter credentials, online contents for public pages are safe to use.
How CSRF Attack Works
There two main type of techniques used in order to perform a CSRF Attack nowadays, both of them are briefly described as follows:
- Cross Site GET Request: In this type of method, the main concept is that the attacker sends a legitimate-looking HTTP request from the victim’s browser.
As a result, the website processes the request without the question, if it is sent by the actual user or from the CSRF attacker. A simple example of a HTTP Get request using the <img> tag. is the following:

- Cross Site POST Request: In this method POST requests can also be equally susceptible to Cross Site GET Request method described earlier. However, a hacker will have to make use of JavaScript in order to succeed such an attack.
The following example of how an CSRF Attack can be abused using POST requests through the use of an <iframe> tag is following:

Mitigation from CSRF Attacks

Nowadays in the cyber community various precautions have been invented to avoid CSRF Attacks. Therefore, it is not impossible to fix this vulnerability. The most widely used methods are the following:
- Same Origin Policy: In this method the main concept is to be sure about the authenticity, or in simple words, the assurance that all the requests originate from trusted sources and not malicious ones. This security measure also ensures that the response from the server is also being sent to the intended application.
- Synchronised (CSRF) Tokens: In this particular kind of precaution, there is an additional surety compared to the “Same Origin Policy”, described above, because special tokens are attached to the session tokens. This measure gives the advantage of secure communication for every update request from the server.
- Double Submit Cookie Policy: In this kind of precaution method, in order to avoid a CSRF Attack, the strategy “Double Submit Cookie” is applied in order to avoid saving a copy of the used token on the server. To be more specific, the server saves the matching token’s value in a cookie instead of keeping it in the live session. At the time the server receives a request, a security check is performed about the legitimate origin of the cookie value.
- CAPTCHA: Although this method is applied to different kind of cyber-attacks, it is also effective against CSRF attack. As described above, CSRF attacks are based on execution of malicious scripts (payloads) by the attacker. This precaution needs user activity such as entering (Letters, Images, etc) that eliminates the exchange of malicious data.
Conclusion
As we described earlier, hopefully the reader of this article will now obtain a full knowledge on how “CSRF Attacks” work and which Mitigation precaution measures need to be considered in order to avoid them.
Important information have also been addressed on how “Synchronized Tokens” and validation of “HTTP” requests work in the cyber community, giving a simplified version to the simple reader and user of current technology.
Hopefully, everyone will be safer on the Web and the Public Authorities will interact with Funding Research opportunities on how to deal with those threats.
We encourage people to report any kind of malicious activity of their personal computing experience to the Local Police Department, as nowadays have created a lot of technologically advanced facilities to investigate further.
Continue Reading:
Introduction to Rainbow Table : Cyber Attack
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj